KeyTalk / Our PKI Certificates Management Platform
KeyTalk CKMS, Our PKI Management Platform

The struggle of complex PKI management
Does your organization also struggle with traditionally complex aspects of PKI Management? Such as Certificate Lifecycle Management (CLM), the enrollment and distribution of hundreds or thousands of certificates for TSL/SSL, S/MIME or device authentication? Or tracking down rogue certificates, integration with Mobile Device Management (MDM) solutions like MS Intune, VMware WS1, or MobileIron, PKI compliance requirements regarding delegated roles and authorizations?
“The KeyTalk Certificate Key Management System (CKMS) offers convenience, insight, overview, and control. Making the PKI implementation, certificate distribution, and management (CLM) easy, organized, and error-free.”
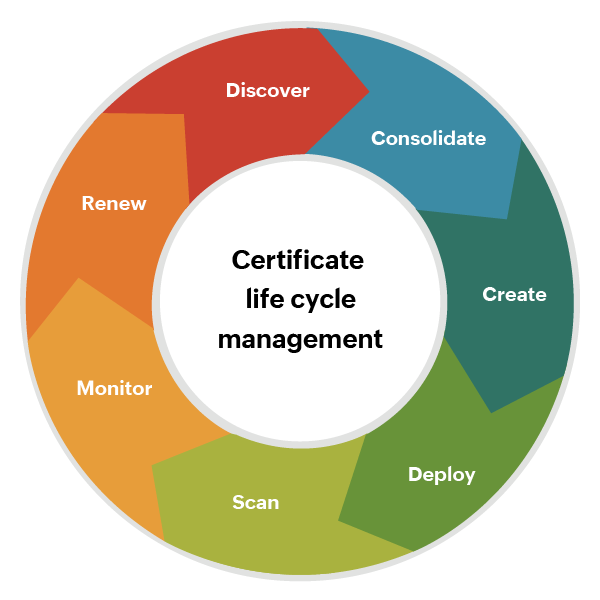
Certificate Lifecycle Management
For most organizations, Certificate Lifecycle Management is a nightmare. We often encounter IT departments that track certificate validity in Outlook calendars or Excel spreadsheets. Or worse, they have no idea how many certificates are scattered across their network. This approach is not only cumbersome but also error-prone and risky.
KeyTalk automates the lifecycle management of your certificates. This provides you with an up-to-date, detailed overview of all private and public certificates and the associated cryptographic keys.
The KeyTalk Smart Security Scan makes it easy to discover existing certificates and keys in your network. Any certificates and keys found can be imported into the KeyTalk CKMS for centralized management.
The future of short lived digital certificates
The CA/Browser Forum decided to drastically reducing the maximum lifespan of publicly trusted SSL/TLS certificates to just 47 days in 2029.
The aim is to mitigate risks associated with longer certificate lifespans, ensuring that certificates are renewed more frequently and thereby improving the overall security posture of web communications.
Organizations that rely on secure web connections and electronic transactions must act upon these developments to ensure ongoing business continuity, maintain efficient operations, and uphold a robust security posture.
The urgency to act upon this new development is now. To ensure your systems, processes and organisation is keeping up and meeting the necessary requirements.

KeyTalk CKMS supports PKI management
The KeyTalk CKMS supports PKI management through:
- Central repository of all internal and external certificates and their corresponding keys, optionally through a certificate discovery process using our Smart Security Scan and importing valid certificates found into our CKMS.
- Automated deployment and renewal of certificates (or semi-automated after notification and authorization) to servers, network devices, and user devices.
- Comprehensive reporting, notifications, and alerts.
- Supporting PKI compliance through centrally configured workflows, delegated roles, and authorizations across departments and subsidiaries. KeyTalk is domain-independent, making it easy to implement in larger organizations.
- Integration with a growing number of Certificate Authorities such as DigiCert, DigiCert QuoVadis, GlobalSign, and Microsoft CA.
- Support for Certificate Revocation List (CRL) and Online Certificate Status Protocol (OCSP).
- Authorization based on MS Active Directory (AD) and MS Azure Active Directory (AAD.)
- Large and expansive number of integrations and supported protocols. For example, Mobile Device Management (MDM) solutions like Intune and MobileIron, load balancers, HSMs, Citrix, SCEP, and ACME.
- Internal CA for issuing private certificates that can also be short-lived.
KeyTalk CKMS Solutions
The KeyTalk CKMS forms the core of the various solutions we provide for:
- TLS/SSL Certificate Lifecycle Management (CLM)
- Secure email based on S/MIME (S/MIME)
- Management and automated distribution of personal certificates for (device) authentication. (DA)
PKI and Certificate Lifecycle Management (CLM) don’t have the best reputation. Implementation, management, and distribution of certificates are known to be complex, cumbersome, error-prone (with potentially significant negative impact), and labor-intensive.
However, it doesn’t have to be that way. KeyTalk’s solutions make PKI Management remarkably simple, efficient, and accurate.


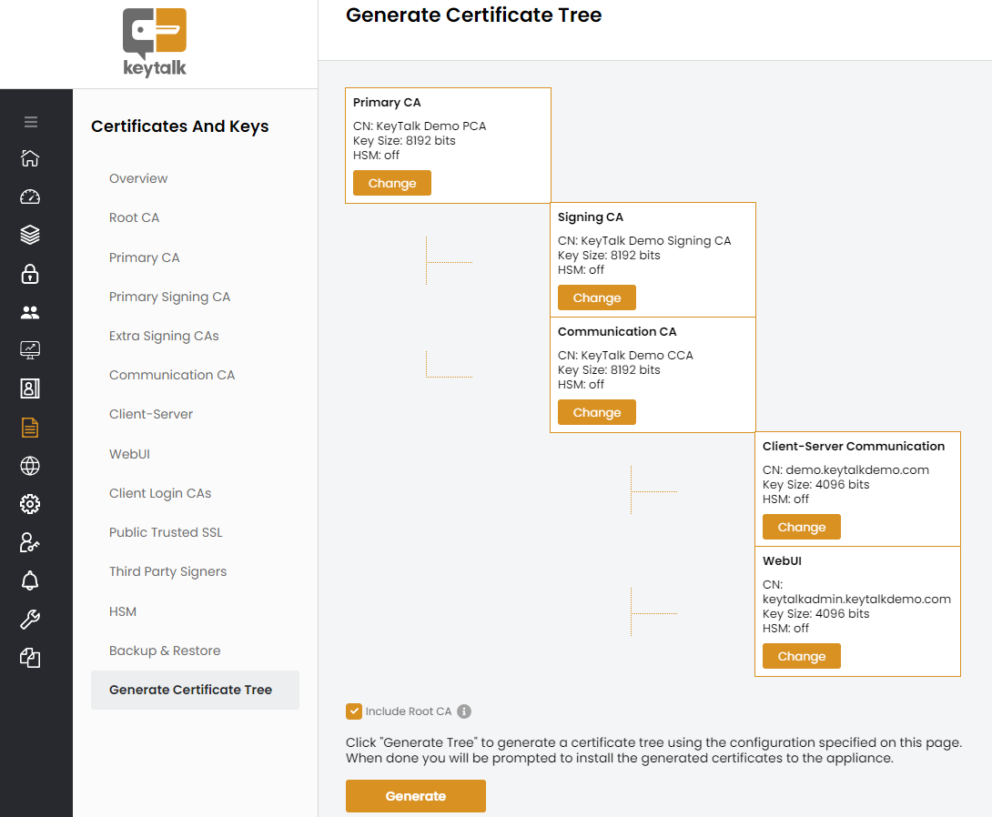
Private CA
In addition to publicly trusted SSL certificates issued by public CAs like DigiCert, GlobalSign, Sectigo, etc., many companies use a private CA, often Microsoft Active Directory Certificate Services.
The KeyTalk CKMS also includes its own private CA, which can be set up and used under an existing Root CA or as a standalone Root CA.
To use an existing Root CA, the existing Root CA certificate with a private key can be uploaded, and then the KeyTalk CKMS will generate its own Intermediate CAs under this Root based on the details provided through the wizard.
Alternatively, a Root CA with a private key can be linked to the KeyTalk CKMS private CA using a supported HSM.
The KeyTalk CKMS private CA can also be used without its own Root CA. In that case, the private CA will generate its own Root CA based on the details provided via the wizard.
In the simplest configuration, setting up your own KeyTalk private CA takes no more than a few minutes, after which internal certificates can already be issued.
Authorization based on AD and AAD
Modern authentication through Microsoft Active Directory (AD) or Microsoft Entra ID offers various features and benefits in combination with the KeyTalk CKMS:
Features:
- Multi-factor authentication: provides additional security by using more than one form of authentication, such as a password and an SMS code.
- Role-based access control (RBAC): restricts access to resources and services based on the user’s role. In the case of KeyTalk admin access, mutation and viewing rights can be assigned through Security Groups. For certificate issuance or access to certificates, Security Groups can be used to assign these rights.

Benefits:
- Security: Modern authentication via AD provides strong security, with support for multi-factor authentication and integration with other Microsoft security solutions.
- Management: User, device, and access rights management can be automated and streamlined, reducing the workload of IT administrators.
- Issue user certificates with attributes from (Azure) AD accounts, such as Email Address, Full Name, Department, and Location. Since KeyTalk is connected to AD/AAD, issued authentication certificates can be stored in AD/AAD (AltSecurityIdentifier), allowing Microsoft systems/software to use the certificates for SSO.
- Issued S/MIME certificates can also be written to AD/AAD, making the issued certificates easily searchable via the Outlook email client through standard synchronization with the (Azure) Global Address List (GAL). Through the AAD connection, the KeyTalk CKMS can verify if a client device is entitled to an Intune SCEP certificate (e.g., for 802.1x).


On Premises, in the cloud, or ‘as a Service’
The KeyTalk CKMS is designed as a Virtual Machine (VM). This means that the underlying OS (Ubuntu), the KeyTalk CKMS application (in C++), and the integrated database (MySQL RDBMS) form a unified entity and can be loaded as an image directly onto VMware or HyperV-based hypervisors. This makes it easy to use in:
- Your own IT infrastructure;
- (Private) cloud environments like AWS, Azure, and Google Cloud;
- As a complete PKI as-a-Service, where the availability and management of the KeyTalk CKMS are fully facilitated by KeyTalk specialists.
There is a lot more we could tell you about the KeyTalk PKI platform, from technical details to use cases and everything in between. So much so that it might be more convenient to answer your questions directly.
Feel free to contact us: our PKI experts will assist you, address specific use cases, and provide demos or proofs of concept upon request.
Check out the KeyTalk solutions for:
- TLS/SSL Certificate Lifecycle Management (CLM)
- Secure Email Service based on S/MIME
- Management and automated distribution of personal certificates for device authentication (DA)
The KeyTalk CKMS Solutions
Three Application Areas
TLS/SSL Certificate Lifecycle Management
Enabling secure Internet communication amongst your connected systems and devices.
Management and Automation of S/MIME Certificates
Provide secure e-mail for both internal and external communication.
How can we help?
Customers like TKE (TK Elevator), TenneT, or Trafigura rely on our easy-to-use solutions and our experience of over 15 years. Agnostic, independent of Certificate Authorities (CAs), managing millions of users and devices.

Request for information
Please fill in the form below and we’ll contact you within 24 hours to find out how we can help you.
