In today’s increasingly complex digital world, ensuring secure communication and data exchange has become crucial. Companies and organizations face challenges such as data breaches, growing cyber threats, and the need to protect sensitive information. This is where Public Key Infrastructure (PKI) comes into play.
In this blog, we explain what PKI is, how it works, the main challenges of traditional PKI management, and why KeyTalk’s CKMS is a powerful solution for automated PKI management.
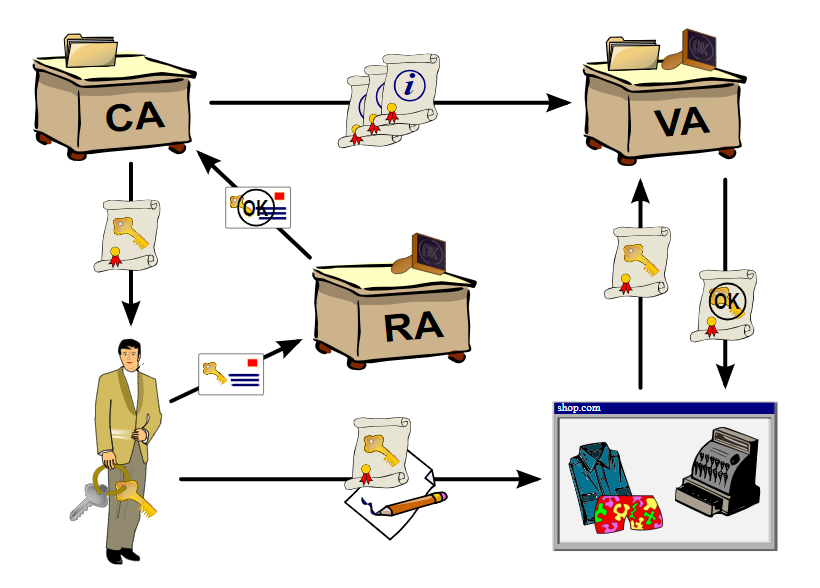
PKI is a system used to create, manage, distribute, store, and revoke digital certificates. These certificates are essential for protecting sensitive information, verifying user identities, and enabling secure communication. PKI uses cryptography with public and private keys, where the public key encrypts the data, and the private key decrypts it. This ensures the integrity and authenticity of digital interactions.
Public Key Infrastructure (PKI) uses advanced encryption methods to ensure secure communication and authentic user identification. It relies on asymmetric cryptography, where two keys play a crucial role: a public key and a private key.
In an asymmetric encryption system, the public key is issued by a trusted certification authority (CA) and can be requested by anyone. The public key is used to verify and authenticate the sender of an encrypted message, so the receiver knows that the message comes from the correct source.
The private key, the other half of the key pair, is strictly confidential and kept only by the receiver. This key is used to decrypt the received encrypted message, ensuring that only the intended recipient has access to the content.
The strength of PKI lies in the combination of these keys. The public key ensures the authenticity of the sender, while the private key guarantees that only the intended recipient can read the message. This methodology ensures a secure and reliable exchange of sensitive information, crucial in a digital world where confidentiality and data integrity are essential.
Public Key Infrastructure (PKI) plays a vital role in ensuring the safety and reliability of digital communication. One of the most important elements of PKI is the certificates, which act as digital identity proofs and strengthen the trust between senders and recipients.
At the heart of a PKI environment are digital certificates, also known as PKI certificates or X.509 certificates. These certificates act as digital passports, verifying the identity of an entity such as a person or organization. Trust is essential here. The receiver of a message must be confident that the sender genuinely holds the identity presented in the certificate.
Another key component of a PKI environment is the Certification Authority (CA). This trusted external authority is responsible for issuing and validating certificates. A CA vouches for the identity of the applicant and confirms this by issuing a digital certificate. Just like a government issues a passport to confirm a person’s identity, CAs ensure the identity of the sender.
A PKI certificate contains several critical pieces of information to ensure the identity and validity of the certificate:
PKI certificates enable secure digital communication by providing a reliable proof of identity, allowing entities such as businesses, individuals, and devices to confirm their digital identity. Without these certificates, it would be much more difficult to trust the authenticity of data and messages transmitted over the internet.
A well-managed PKI environment, supported by trustworthy certification authorities, forms the backbone of a secure digital world. Therefore, it is crucial to ensure robust PKI management and timely renewal of certificates, so the integrity of digital communication remains safeguarded.
Managing PKI certificates manually can be cumbersome and error-prone. Constant monitoring of certificates and the need to renew them on time place a significant burden on IT departments. Without a centralized management system, the loss of control or expiration of certificates can lead to downtime, security breaches, and disruption of business activities.
To address these challenges, KeyTalk now offers a hybrid Certificate & Key Management System (CKMS), available both on-premises and from the cloud. This solution automates the entire certificate lifecycle, from issuance to renewal and revocation, and provides extensive support for multiple public CAs, including DigiCert, GlobalSign, Sectigo, and private CAs like Microsoft AD CS and EJBCA/PrimeKey.
As the complexity of digital security continues to grow, using advanced PKI management systems like KeyTalk’s CKMS is essential to protect data, automate processes, and ensure overall security. With the ability to manage PKI from the cloud, KeyTalk offers organizations the flexibility to future-proof their security infrastructure.
Are you interested in what KeyTalk CKMS can do for your organization? Contact us today and discover how we can help optimize your PKI management.