As the new year just started, it is important to consider the prominent developments in Certificate Lifecycle Management (CLM) for 2026. Cybersecurity architecture has become a crucial agenda item for the C-Suite due to its significant impact on IT strategy and business operations. CLM plays a pivotal role in ensuring safe and secure business communication by managing the complex lifecycle of digital certificates effectively.
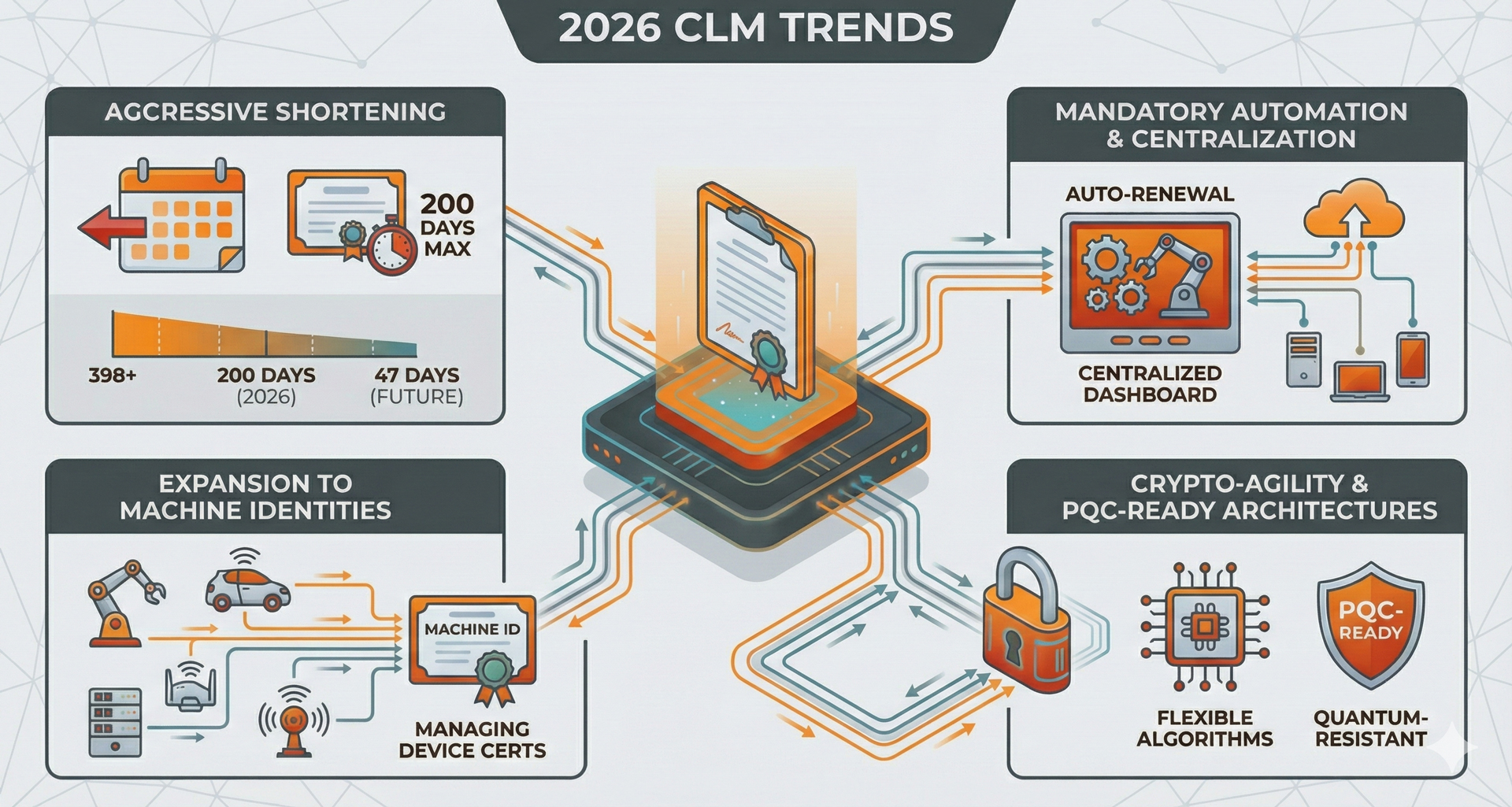
The main 2026 trends in certificate lifecycle management (CLM) are aggressive shortening of certificate lifetimes, mandatory automation and centralization, expansion to machine identities, and crypto-agility, PQC-ready architectures. In this blogpost we go more in detail on these topics.
Starting 15th of March 2026, publicly trusted TLS certificates will be limited to a maximum validity of 200 days, with further reductions to 100 days in 2027 and just 47 days by 2029. These shorter lifetimes multiply renewal workloads several-fold, making manual tracking via spreadsheets or ticket queues operationally unsustainable and pushing organizations toward automated, end-to-end certificate lifecycle management (CLM).
To keep pace, CLM platforms must automate discovery of all certificates—public and private—enforce policy-driven issuance and renewal, and automatically deploy updates to load balancers, applications, and proxies. Centralized dashboards and APIs are becoming table stakes, replacing siloed CA portals and enabling consistent governance and alerting for expiry, mis-issuance, and policy drift.
With the continued expansion of cloud, containers, microservices, and IoT, most new certificates in 2026 will belong to non-human identities, significantly increasing the scale and complexity that CLM must handle. As a result, CLM is being embedded directly into DevOps and platform tooling—such as Kubernetes, service meshes, and service identity systems—so certificates are provisioned and rotated automatically alongside workloads.
Shorter lifetimes also serve as preparation for postquantum cryptography, so CLM systems need to support algorithm agility, hybrid (classical plus PQ) certificates, and staged migrations. Accordingly, 2026 roadmaps focus on inventorying cryptography, classifying high-risk systems, and proving that CLM workflows can swap key types and certificate profiles safely without causing outages.
The certificate lifecycle management (CLM) software market is projected to grow rapidly through 2026, with the most significant growth occurring in automation and AI-driven segments. Vendors are increasingly incorporating AI features into their offerings, such as the ability to locate rogue or unmanaged certificates, forecast renewal peaks, and identify compliance gaps as certificate volumes and renewal velocity continue to rise.
Amid rising geopolitical tensions, US–EU legal conflicts such as the CLOUD Act, and heightened critical infrastructure risk, regulators are treating data sovereignty as a core design constraint for systems and architectures. New and upcoming EU frameworks—including the EU Cloud Sovereignty Framework, EUCS, NIS2, DORA, the EU Data Act, and the Cloud & AI Development Act—are pushing organizations to prove where data is stored, which jurisdiction applies, and how independent they are from non-EU hyperscalers. Consequently, encryption, key management, and PKI are being redesigned so customers—not foreign cloud providers—hold and control the keys, a defining feature of sovereign cloud designs.
The sectors most exposed in 2026 are those that are both heavily regulated on sovereignty and critically dependent on certificates and machine identities: finance, healthcare, public sector/defense, and critical infrastructure (energy, transport, telecom, cloud providers).
Organizations in these sectors will need CLM that can both handle short-lived, high volume certificates and enforce data residency, CA choice, and key custody rules consistent with sovereign architecture requirements. That typically means consolidating onto centralized, automated CLM platforms that support regional PKI deployments, sovereign or EU only CAs, and detailed reporting for NIS2/DORA and cloud sovereignty audits.
KeyTalk CKMS is an automated certificate lifecycle management (CLM) platform that enables organizations to issue, manage, and revoke certificates swiftly and efficiently. By eliminating manual processes, companies using our platform can easily adhere to policies and procedures and stay ahead of the evolving changes driven by the CA/B Forum.
From a single, centralized dashboard, IT administrators can effortlessly manage the entire certificate environment with KeyTalk CKMS. This single point of control not only simplifies day-to-day tasks but also facilitates seamless switching between Certificate Authorities (CAs) or connecting with alternative cloud providers for platform hosting.
KeyTalk has been proactively preparing for the transition to post-quantum cryptography and is pleased to announce that we are in the final stages of updating our platform to support this upcoming shift.
KeyTalk’s standout feature is its CA-independence, empowering companies to choose their preferred public certificate source. Additionally, KeyTalk can distribute private certificates within your own IT network. With a sovereign design at its core, KeyTalk offers flexible deployment methods to suit your organization’s needs, whether that’s on-premise, hybrid, or fully cloud-based.
Do you have questions about this article or how KeyTalk CKMS helps you ease with the management and automation of digital certificates? Our support team is available 24/7 to assist and guide you in implementing a fully automated PKI architecture via e-mail or our contact page.
The KeyTalk Team